
Ransomware is malicious software that allows a hacker to restrict access to an individual’s or company’s critical information in some way and then demand some form of payment to lift the restriction. The most common form of restriction today is encryption of important data on the computer or network, which essentially lets the attacker hold user data or a system hostage, and message may be looks like “!!! IMPORTANT INFORMATION!!! All of your files are encrypted with RSA-2048 and AES-128 ciphers.” or we might see a readme.txt stating, “Your files have been replaced by these encrypted containers and aren’t accessible; you will lose your files on [a Date value] unless you pay $2000 in Bitcoin.” As it is malware and installed covertly on a system and executes a Cryptovirology (Cryptovirology is a field that studies how to use cryptography to design powerful malicious software.) attack that locks or encrypts valuable files on the systems/networks. Without a comprehensive network segmentation or micro-segmentation policy, malicious actors can also move laterally within organization’s network, infect endpoints and servers, and demand a ransom for access to the valuable data.
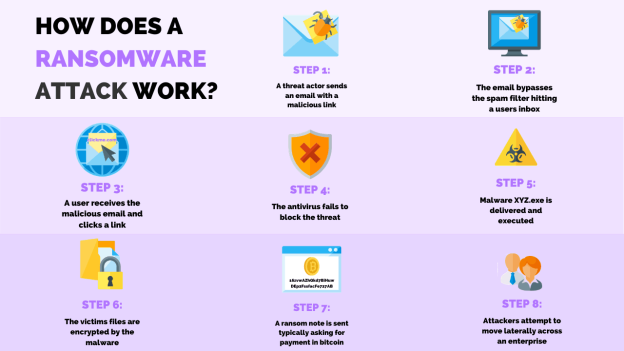
The Current State of Ransomware
Below infographic presents eye-opening facts that demonstrate the danger behind this cyber threat.

Types of Ransomwares
Ransomware attacks can be deployed in different forms. Some variants may be more harmful than others, but they all have one thing in common: a RANSOM.
1) Crypto malware
2) Lockers
3) Scareware
4) Doxware
5) RaaS
6) Mac ransomware – KeRanger
7) Ransomware on mobile devices
Preventing Ransomware
There are many steps organizations can take to prevent ransomware with varying degrees of effectiveness. Below are few tips for actions can take to reduce risk of a ransomware attack:
|
|
Action |
Description |
|
1 |
Staff Awareness |
Raising awareness about ransomware is a baseline security measure. But it could only take one employee lowering their guard for an organization to be compromised. As training sessions have little influence over staff for every potential attack, it makes added security more imperative. |
|
2 |
Spam Filter |
Cybercriminals send millions of malicious emails to at-random organizations and users, but an effective spam filter that continually adapts alongside a cloud-based threat intelligence center can prevent more than 99% of these from ever reaching employees’ desktops. |
|
3 |
Configure Desktops Extensions |
Employees should be trained not to double-click on executable files with a .exe extension. However, Windows hides file extensions by default, allowing a malicious executable such as “evil.doc.exe” to appear to be a Word document called “evil.doc”. Ensuring that extensions are always displayed can go a long way to countering that kind of threat. |
|
4 |
Block Executables |
Filtering files with a .exe extension from emails can prevent some malicious files from being delivered to employees, but bear in mind that this isn’t foolproof. Malicious emails can instruct employees to rename files, and ransomware is also increasingly being delivered as JavaScript files (see below). |
|
5 |
Block Malicious JavaScript Files |
Ransomware being delivered in .zip files containing malicious JavaScript files are common. These are disguised as text files with names like “readme.txt.js” – and often just visible as “readme.txt”, with a script icon for a text file. You can prevent this vulnerability for staff by disabling Windows Script Host. |
|
6 |
Restrict Use of Elevated Privilege |
Ransomware can only encrypt files that are accessible to a particular user on their system – unless it includes code that can elevate a user’s privileges as part of the attack, which is where patching and zero trust come into play. |
|
7 |
Promptly Patch Software |
It’s a basic security precaution to ensure that all software is updated with the latest security patches, but it’s worth reiterating because breaches continue due to prolonging updating. Just in 2020, the SolarWinds hack could’ve been prevented for organizations that promptly patch software. |
|
8 |
Zero Trust |
Moving toward zero trust offers visibility and control over your network, including stopping ransomware. The next three actions: prioritize assets and evaluate traffic, microsegmentation, and adaptive monitoring are central steps of the zero trust architecture and greatly reduce your risks of an attack. |
|
9 |
Prioritize Assets and Evaluate Traffic |
With the use of inventory tools and IOC lists, an organization can identify its most valuable assets or segments. This full picture offers staff a look into how an attacker could infiltrate your network and gives needed visibility into traffic flows. This gives your team clear guidelines as to what segments need added protection or restrictions. |
|
10 |
Microsegmentation |
Microsegmentation is the ultimate solution to stopping lateral movement. By implementing strict policies at the application level, segmentation gateways and NGFWs can prevent ransomware from reaching what’s most important. |
|
11 |
Adaptive Monitoring and Tagging |
Once your micro-perimeters surround your most sensitive segments, there’s a need for ongoing monitoring and adaptive technology. This includes active tagging of workloads, threat hunting, and virus assessments, and consistent evaluation of traffic for mission-critical applications, data, or services. |
|
12 |
Utilize a CASB |
A cloud access security broker (CASB) can help manage policy enforcement for your organization’s cloud infrastructure. CASBs provide added visibility, compliance, data security, and threat protection in securing your data. |
|
13 |
Rapid Response Testing |
In the event of a successful breach, your team must be ready to restore systems and data recovery. This includes pre-assigning roles and ensuring a plan is in place. |
|
12 |
Sandbox Testing |
A common method for security analysts to test new or unrecognized files is by utilizing a sandbox. Sandboxes provide a safe environment, disconnected from the greater network for testing the file. |
|
13 |
Update Anti-Ransomware Software |
As noted, consistent updating of network software is critical. This is especially true for your existing intrusion detection and prevention system (IDPS), antivirus, and anti-malware. |
|
14 |
Offline Backups |
While virtual backups are great, if you’re not storing data backups offline, you’re at risk of losing that data. This means regular backups, multiple copies saved, and monitoring to ensure backups hold true to the original. Restoring data after an attack is often your best approach. |
|
15 |
Update Email Gateway |
All email for your network typically travels through a secure web gateway (SWG). By actively updating this server, you can monitor email attachments, websites, and files for malware. This visibility into attacks trending for your organization can help inform staff moving forward of what to expect. |
|
16 |
Block Ads |
All devices and browsers should have extensions that automatically block pop-up ads. With the extensive use of the internet, malicious ads pose a long-lasting threat if not blocked. |
|
17 |
Bring-Your-Own-Device (BYOD)Restrictions |
If you have a remote work staff or just a loose policy surrounding devices acceptable for network access, it might be time to crack down. Unregulated use of new or unique devices poses an unnecessary risk to your network. Enterprise mobility management (EMM) is one solution. |
|
18 |
Forensic Analysis |
After any detection of ransomware, there needs to be an investigation into its entry point, time in the environment, and confirm that it’s been fully removed from all network devices. From there, the task of ensuring it never returns begins. |
Network Security Monitoring Tools

The most common Network Security monitoring tools are as,
|
Argus |
|
|
POf |
|
|
Nagios |
|
|
Splunk |
|
|
OSSEC |
Encryption Tools

|
Tor |
|
|
KeePass |
|
|
TrueCrypt |
Web Vulnerability Scanning Tools
|
Burp Suite |
|
|
Nikto |
|
|
Paros Proxy |
|
|
Nmap |
|
|
Nessus |
|
|
Nexpose |
Penetration Testing

|
Metasploit |
|
|
Kali Linux |
Password Auditing Tools
|
John the Ripper |
|
|
Cain and Abel |
|
|
Tcpdump |
|
|
Wireshark |
Network Defense Wireless Tools

|
Aircrack |
|
|
NetStumbler |
|
|
KisMAC |
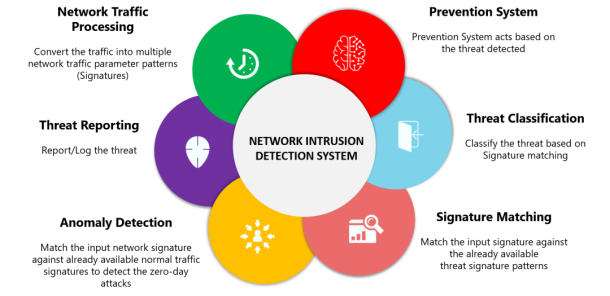
Network Intrusion & Detection
|
Snort |
|
|
Forcepoint |
https://www.forcepoint.com/product/ngfw-next-generation-firewall |
|
GFI LanGaurd |
|
|
Acunetix |
Ransomware attack solutions
One of the most important ways to stop ransomware is to have a strong endpoint security. This is a program that blocks malware from infecting your systems when installed on endpoint devices such as phones and computers. Just be sure that ransomware protection is included as many traditional anti-virus products are not equipped to defend against modern ransomware attacks. As ransomware is commonly delivered through email, email security is key in preventing ransomware. Secure email gateway technologies filter email communications with URL defenses and attachment sandboxing to identify threats and block them from being delivered to users. This stops ransomware from arriving on endpoint devices while blocking users from inadvertently installing malicious programs onto their machines. DNS web filtering solutions stop users from visiting dangerous websites and downloading malicious files, blocking ransomware that is spread through viruses downloaded from the Internet, including Trojan horse software. DNS filters also block malicious third-party adverts. Isolation technologies completely remove threats from users by isolating browsing activity in secure servers and displaying a safe render to users. Moreover, isolation does not affect the user experience, delivering high security efficacy and seamless browsing. Below are few key points to be noted and needs to implement as practice to prevent & limit the impact of Ransomware.
1) Perform regular system backups
2) Segment your network
3) Conduct regular network security assessments
4) Conduct employee security training
5) Get your password security under control
6) Ransomware Insurance
Ransomware : Infographic



This is a really good article.
LikeLike